
11 Tahun Kerja Lalu Diberhentikan, Programer Ini Balas Perusahaannya Sekali Klik, Rugi Jutaan Dollar - Tribun-timur.com

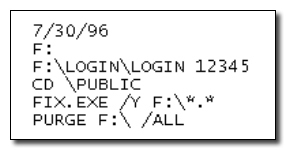
In the Tim Lloyd logic bomb attack on Omega Engineering, what type of vulnerability was the existence of the user "12345" an example of? | Study.com















![Charles Lloyd - 8: Kindred Spirits (Live From The Lobero) [CD/DVD] - Music Charles Lloyd - 8: Kindred Spirits (Live From The Lobero) [CD/DVD] - Music](https://m.media-amazon.com/images/I/71iLvHKe0YL._SL1200_.jpg)


